Anonymous User Enrollment Flow
The anonymous enrollment flow allows a user to be created and bound to a device without requiring any UI interaction or additional input.
-
A unique user ID is automatically generated (using a random UUID) and linked to the device.
-
The user is silently created in the Identity Provider (IDP) without any interaction or input, ensuring a seamless experience without requiring details like email or username.
-
No identity verification is performed, as the enrollment remains completely anonymous.
Steps in Anonymous Enrollment Flow
| Step | Authenticator | Description |
|---|---|---|
| AST Device Activation | KOBIL AST Login | Perform AST Activation to get the AST Client ID for the user. |
| Risk Evaluation | KOBIL Device Risk Evaluator | Evaluate the risk level based on the response from AST Activation. |
| Anonymous User Creation | KOBIL Create Account | Automatically creates a user in the IDP with a randomly generated UUID. |
| AST Device Link | KOBIL AST Login | Links the newly created user to the AST Client ID. |
| Assigning User Group | KOBIL User Group Registration | Assigns the ks-user group to the created user. |
| ACR and AMR Computation | KOBIL AST Claims | Computes ACR and AMR values and stores them in the session. |
At the end of the Anonymous Enrollment Flow, the anonymous user is automatically added to the ks-user group. The process generates an authorization code that can be used to request an access token for further exchange or authorization with third-party applications.
Example Access Token
{
"exp": 1742322862,
"iat": 1742322562,
"auth_time": 1742322548,
"jti": "6695366a-4b29-4ff7-8a5c-dd205675202b",
"iss": "https://idp.gondor-grootan-kc22-dev-1yymr.gondor.dev.kobil.com/auth/realms/idpdocs",
"aud": [
"ast-services",
"ks-users",
"account"
],
"sub": "97750b0f-148e-4d22-98ff-06a268174a2c",
"typ": "Bearer",
"azp": "AnonymousUserEnrollment",
"nonce": "5vfr1ckktx7",
"session_state": "92623807-ab8c-42f8-849f-3fd977ad9b02",
"acr": "0",
"realm_access": {
"roles": [
"default-roles-thorstenworkspace",
"digitanium_user",
"offline_access",
"uma_authorization"
]
},
"resource_access": {
"ast-services": {
"roles": [
"ast-client"
]
},
"ks-users": {
"roles": [
"ast-client"
]
},
"account": {
"roles": [
"manage-account",
"manage-account-links",
"view-profile"
]
}
},
"scope": "openid profile email acr0",
"sid": "92623807-ab8c-42f8-849f-3fd977ad9b02",
"email_verified": false,
"amr": [
"mvk"
],
"tenantId": "idpdocs",
"preferred_username": "97750b0f-148e-4d22-98ff-06a268174a2j",
"astClientId": "01JPN88EX93MEB49KAQDCMMNEZ"
}
How to configure the flow
The Anonymous Enrollment Flow is automatically set up during realm creation.
-
The client "AnonymousUserEnrollment" is created as part of the realm setup with the AST client scope.
-
This “AnonymousUserEnrollment” client is configured with the Browser Flow linked to the AnonymousDeviceEnrollment flow.
-
The KOBIL AST Claims authenticator must be added to the flow manually. Refer to Step 4 for details.
Step 1 : Create a Client
-
Navigate to the Keycloak Admin Console.
-
Go to Clients → Click Create.
-
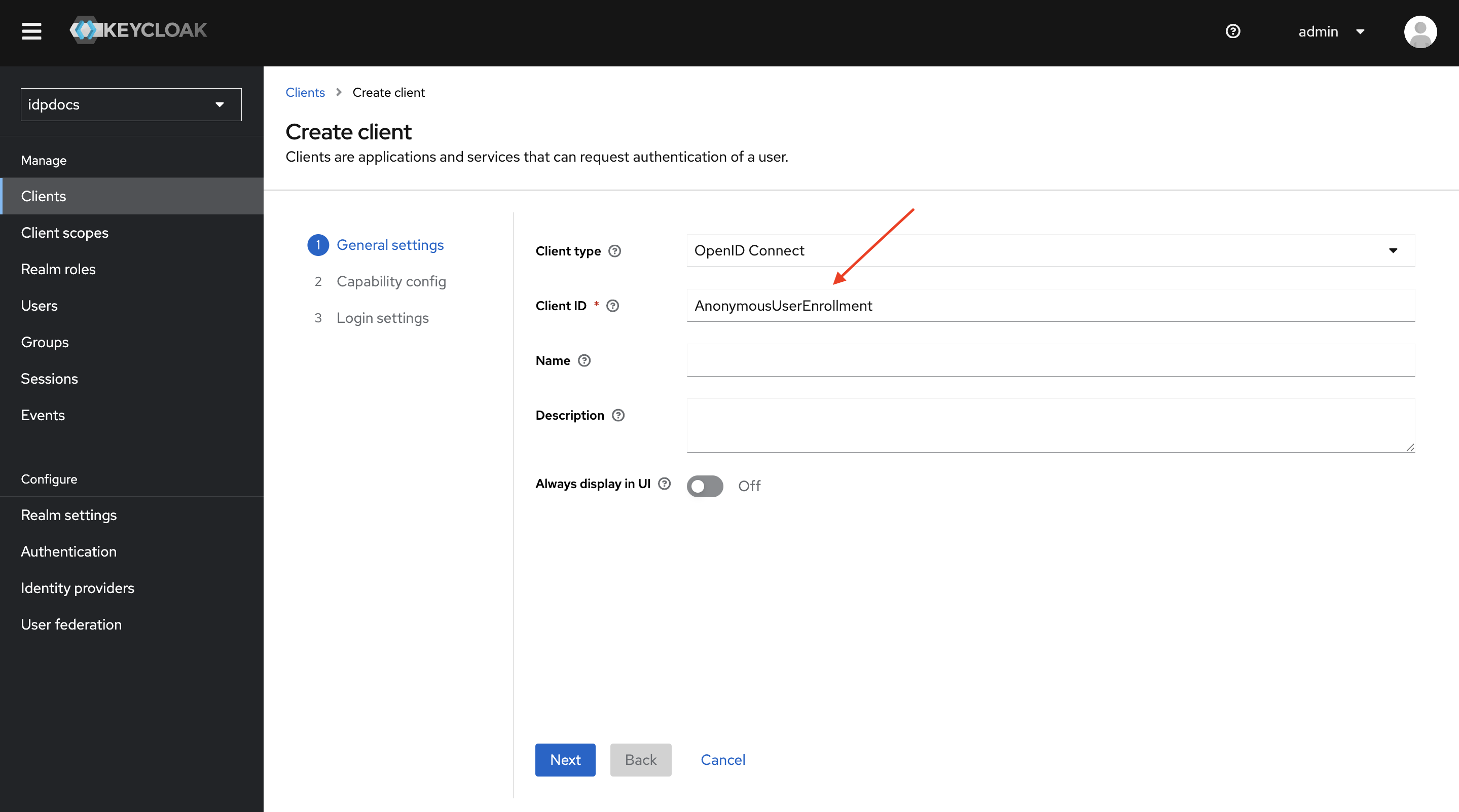
Enter a Client ID and Click next.
-
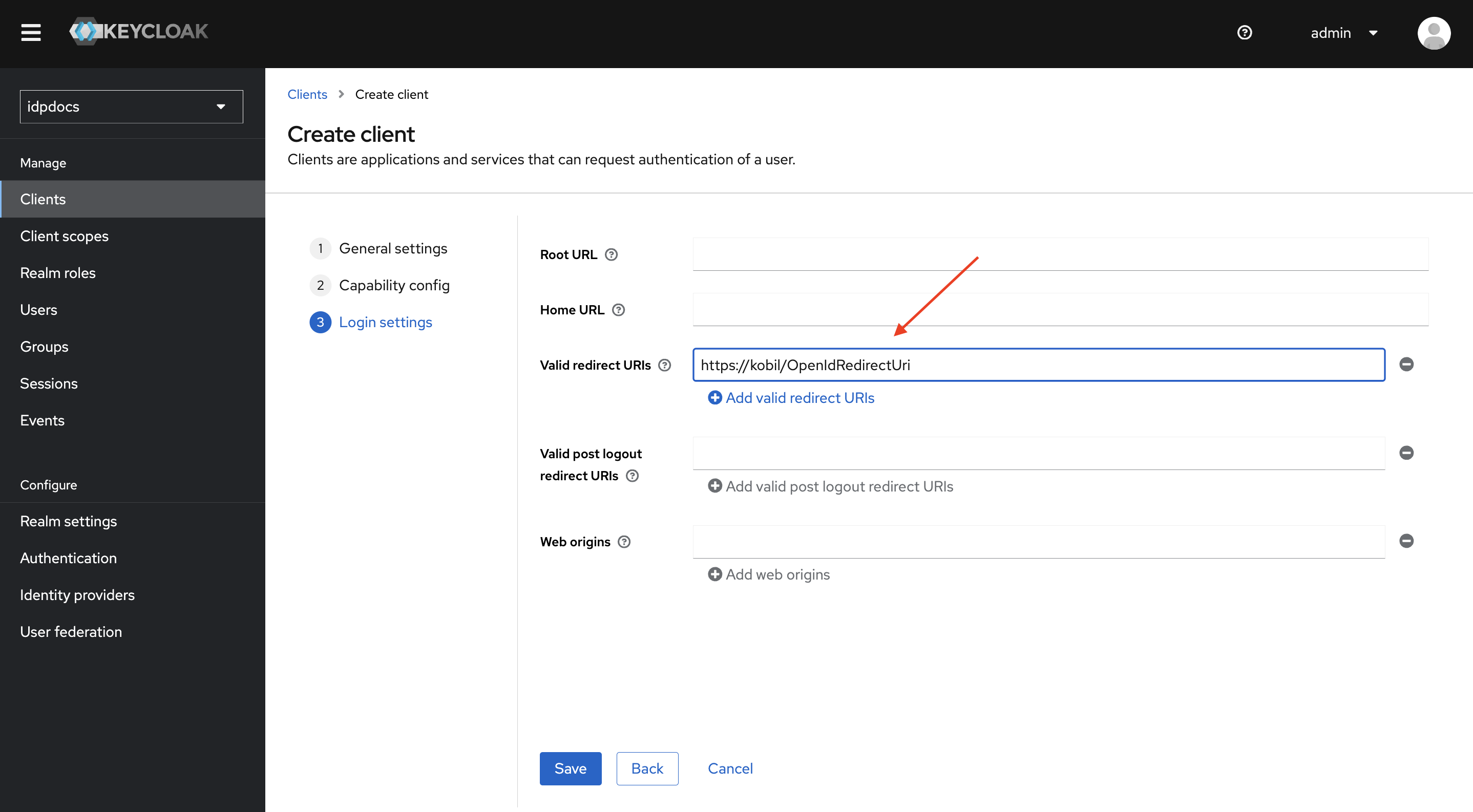
In the Valid Redirect URIs field, enter the appropriate redirect URI(s) and Click Save to create the client.
Step 2 : Assign AST Scope to the Client as a Default Scope
- Go to the created client → Click client scopes.
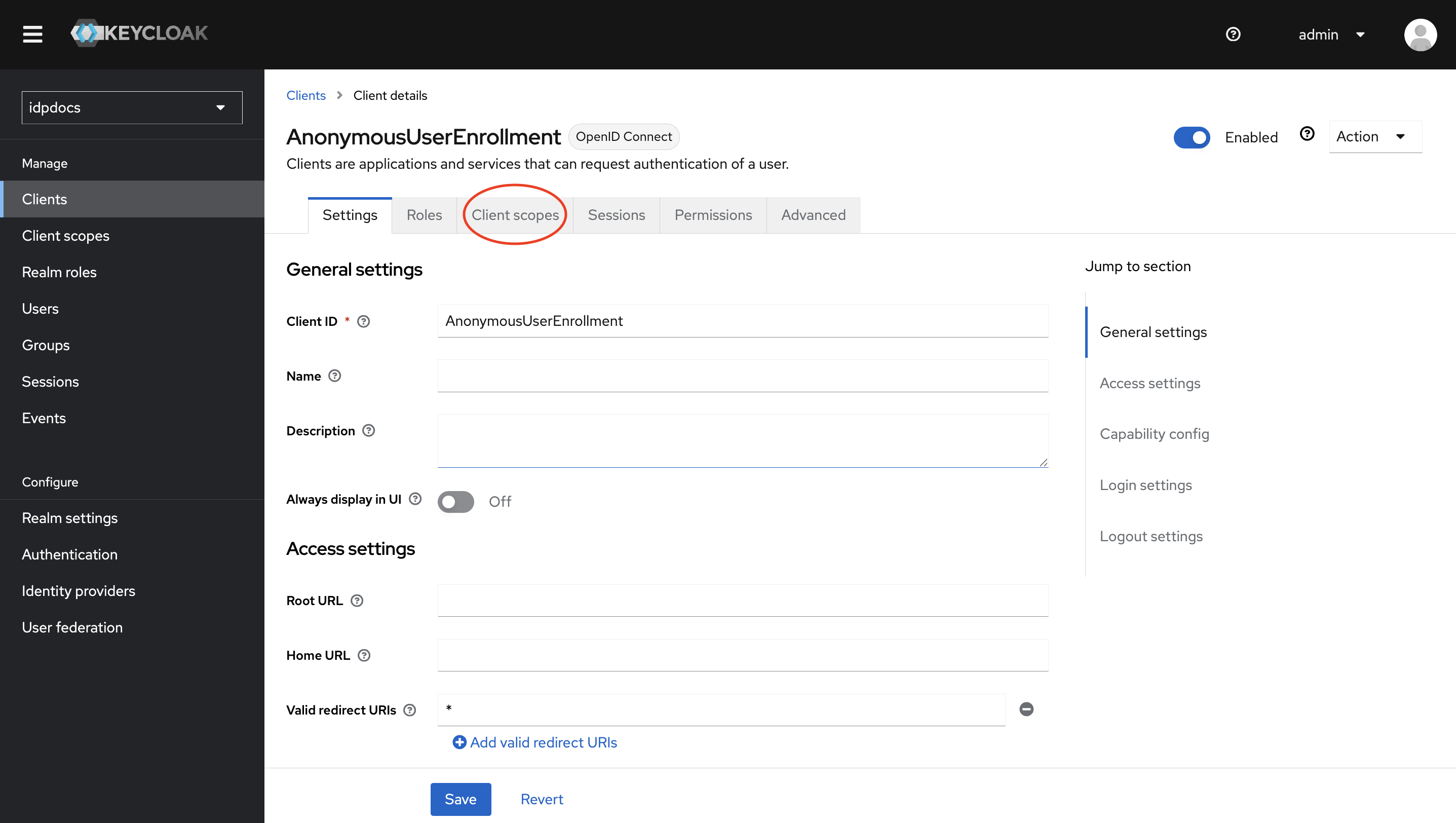
- Click on Add client scope.
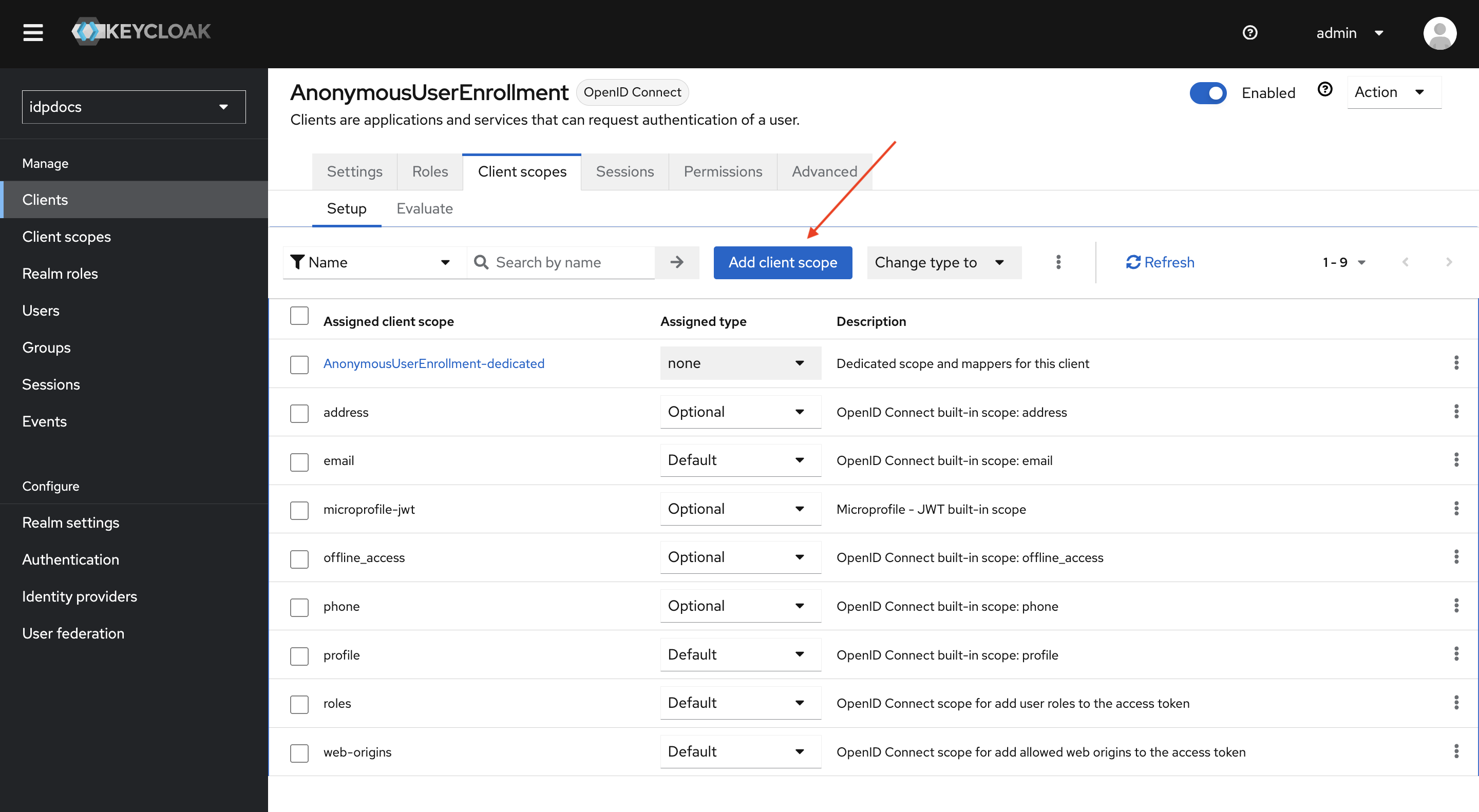
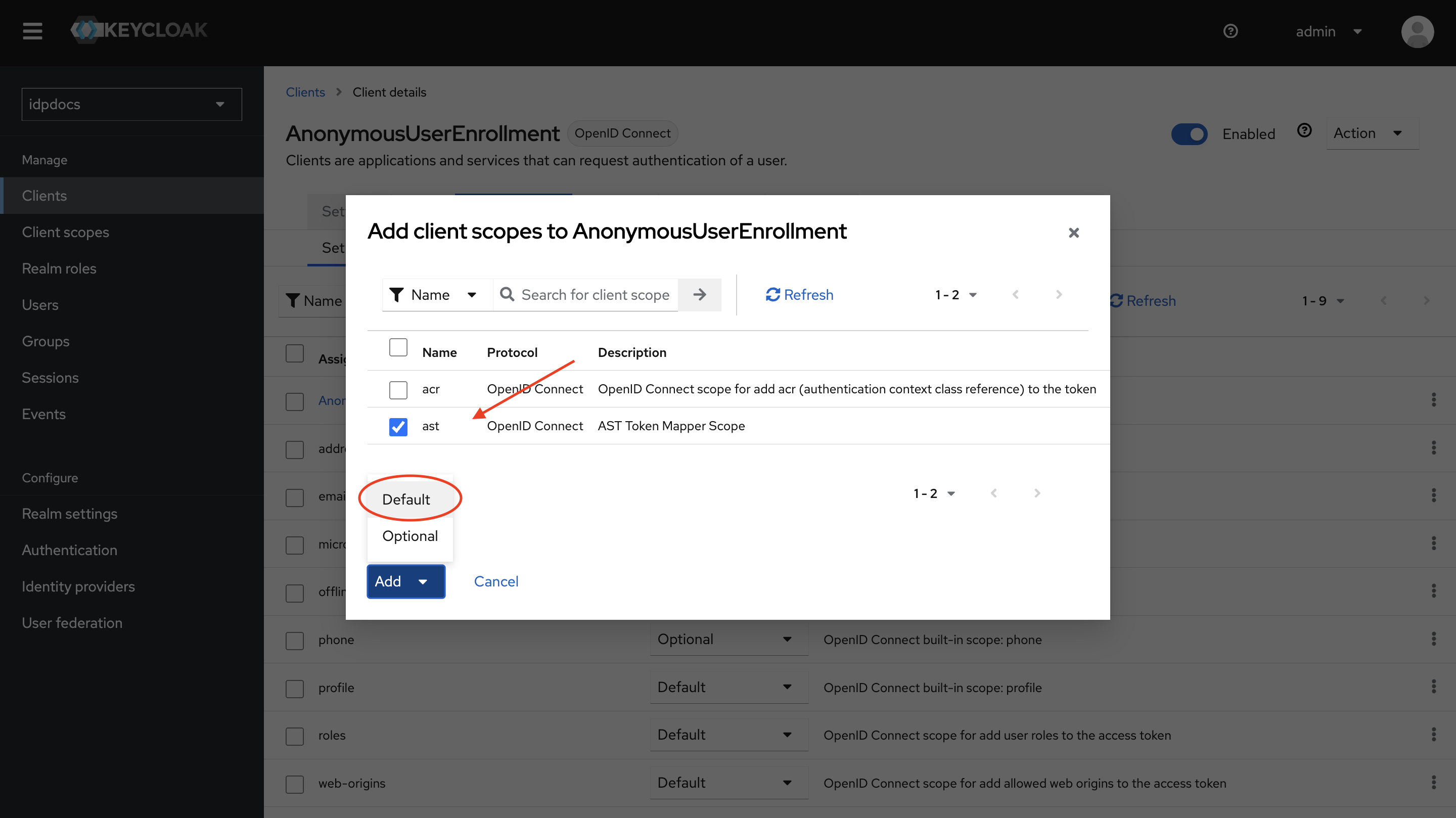
- Select the ast scope, click Add, then choose Default. This will assign the ast scope to the client.
Step 3 : Set Browser flow to the client
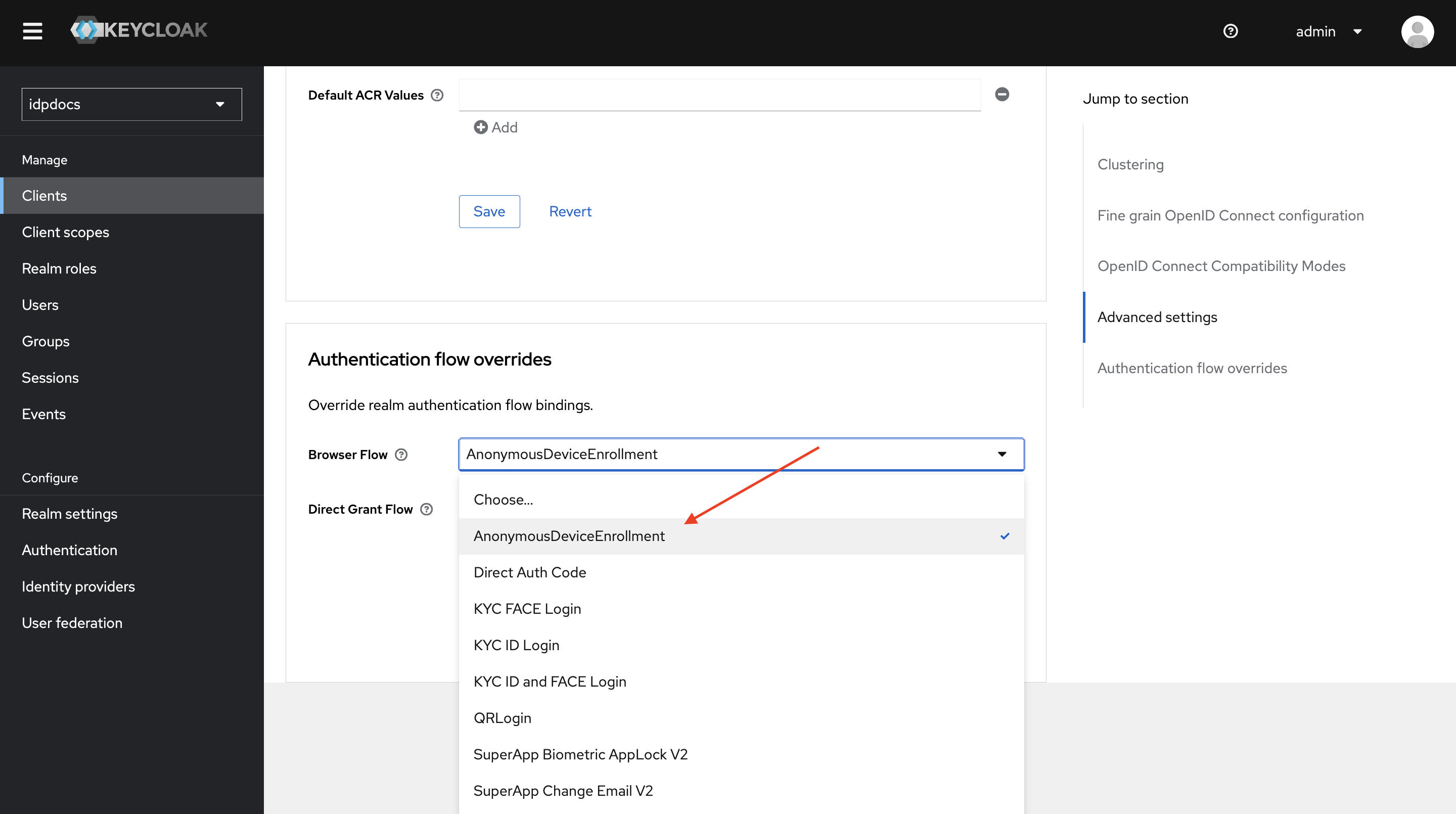
-
Navigate to Clients, select the AnonymousUserEnrollment client, go to the Advanced tab, and scroll to the bottom of the page.
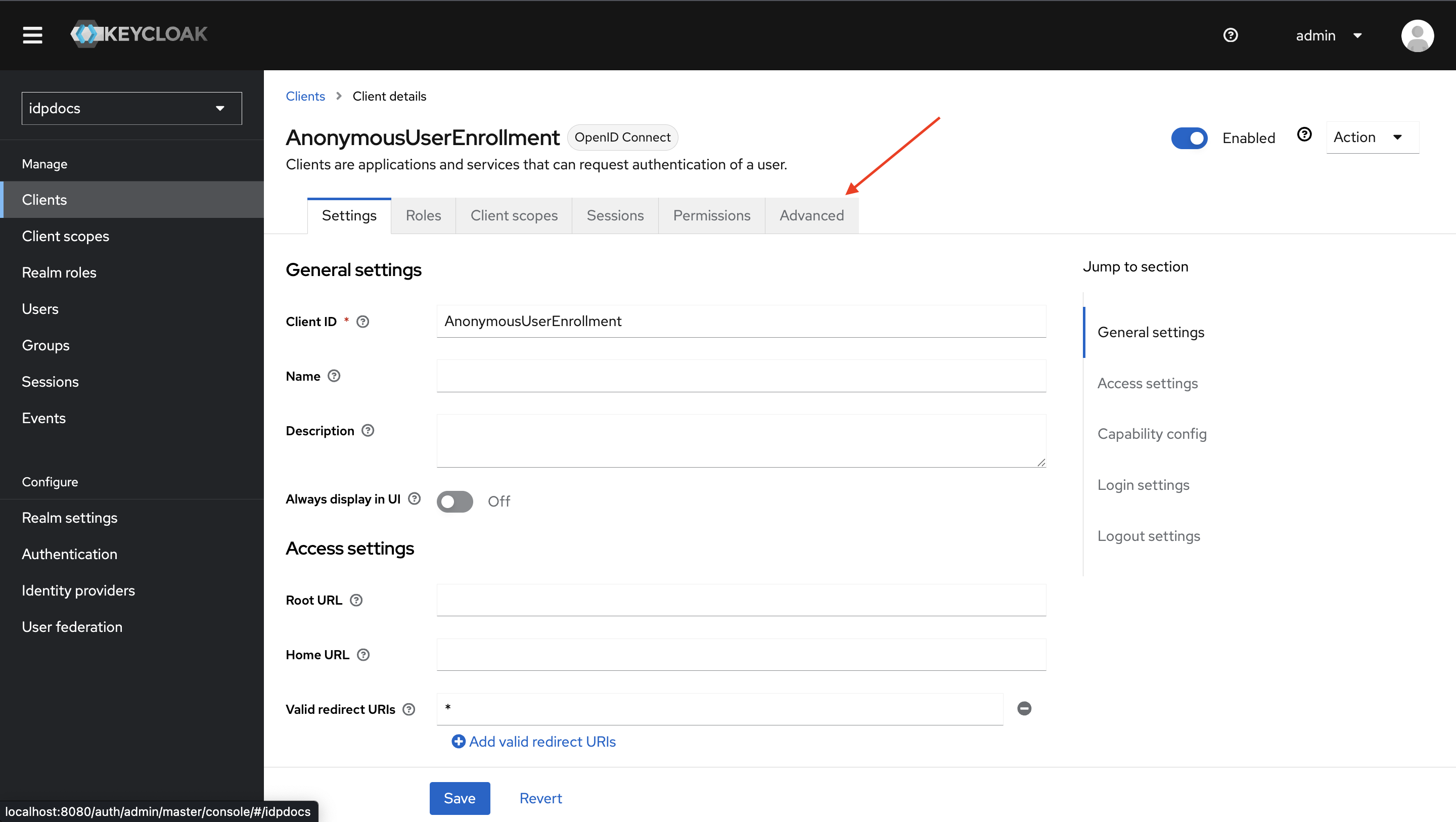
-
Set Browser flow as AnonymousDeviceEnrollment..
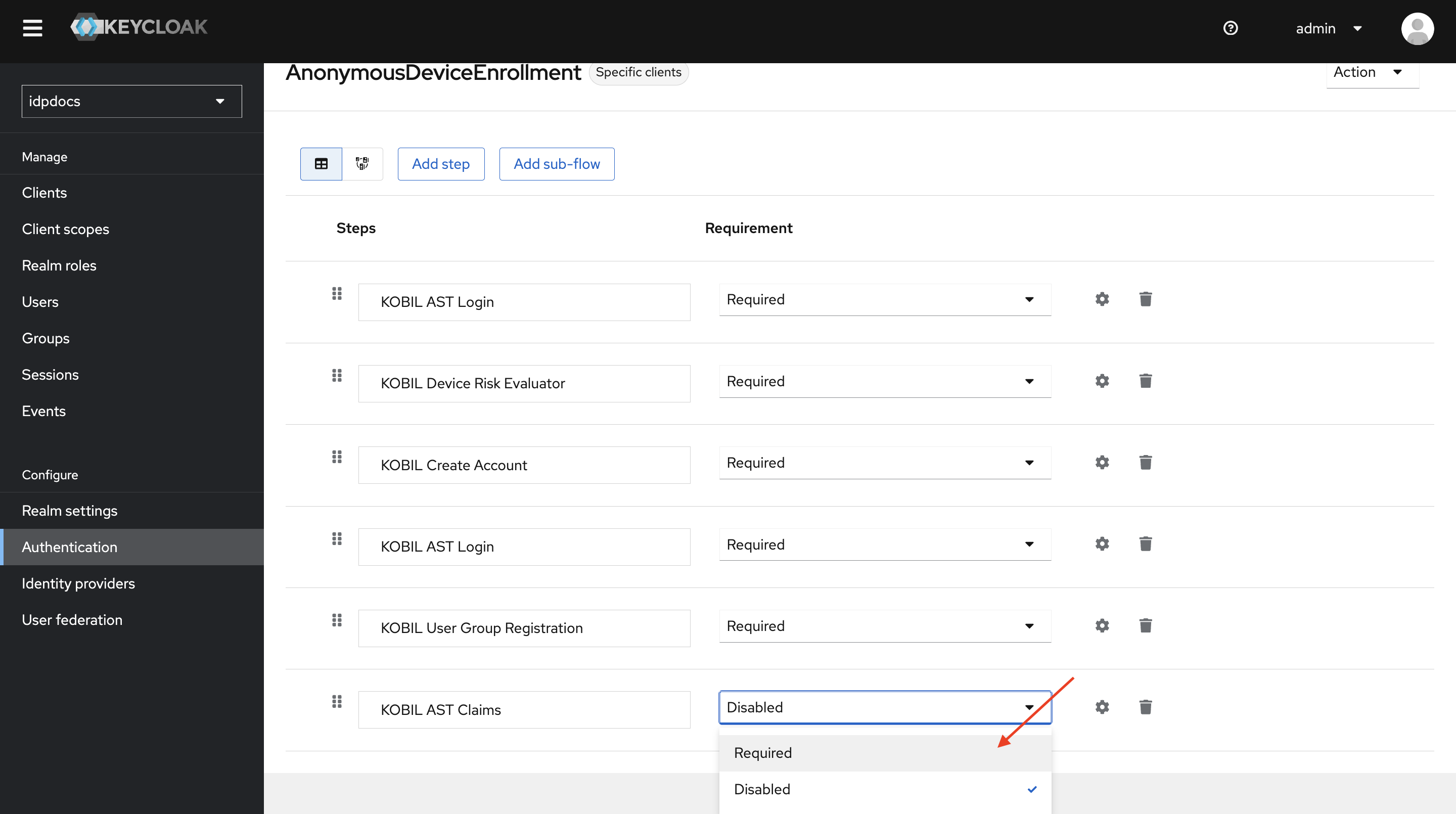
Step 4 : Add KOBIL AST Claims authenticator to the AnonymousDeviceEnrollment flow
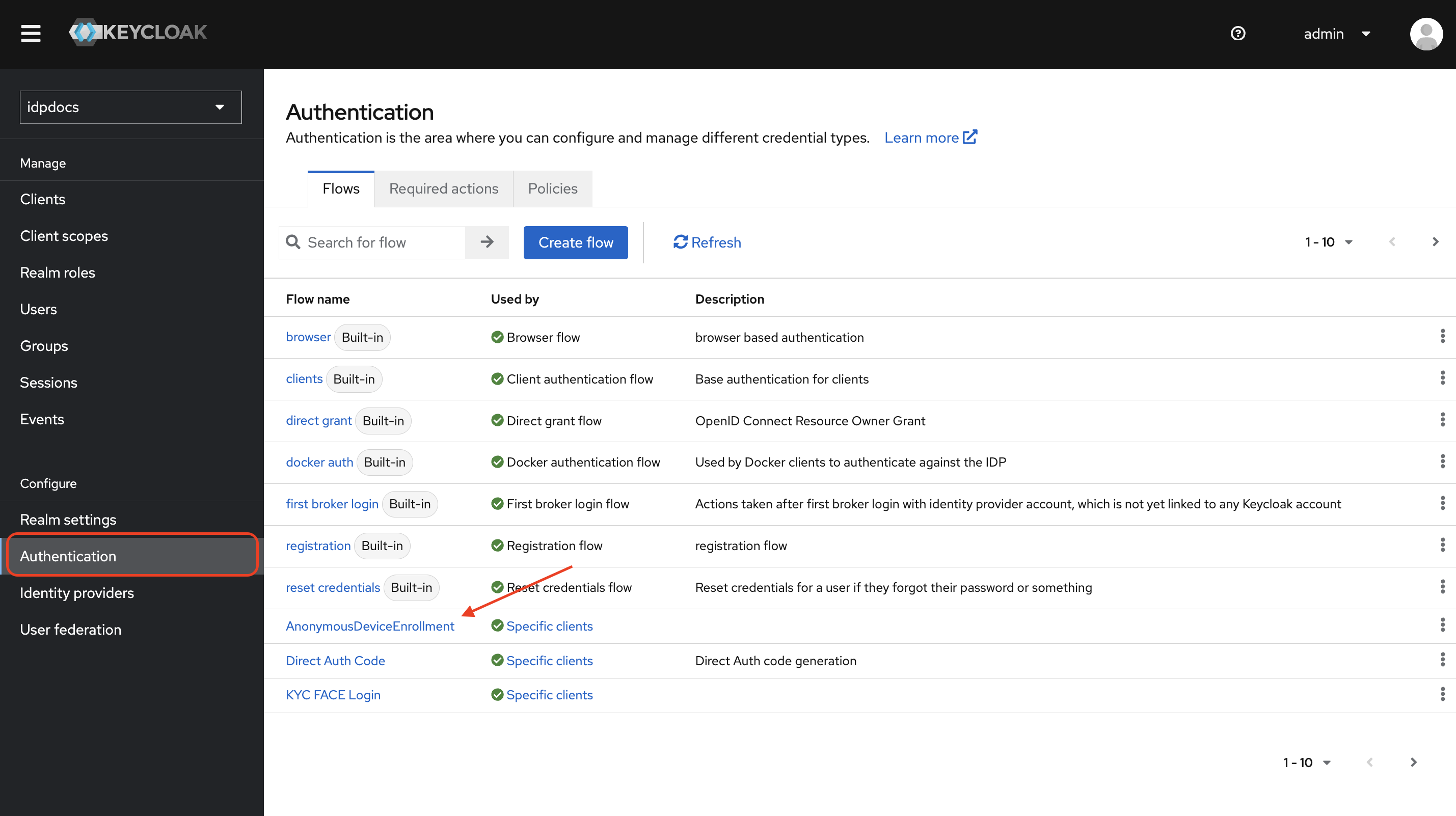
-
Navigate to Authentication section and click on AnonymousDeviceEnrollment flow.
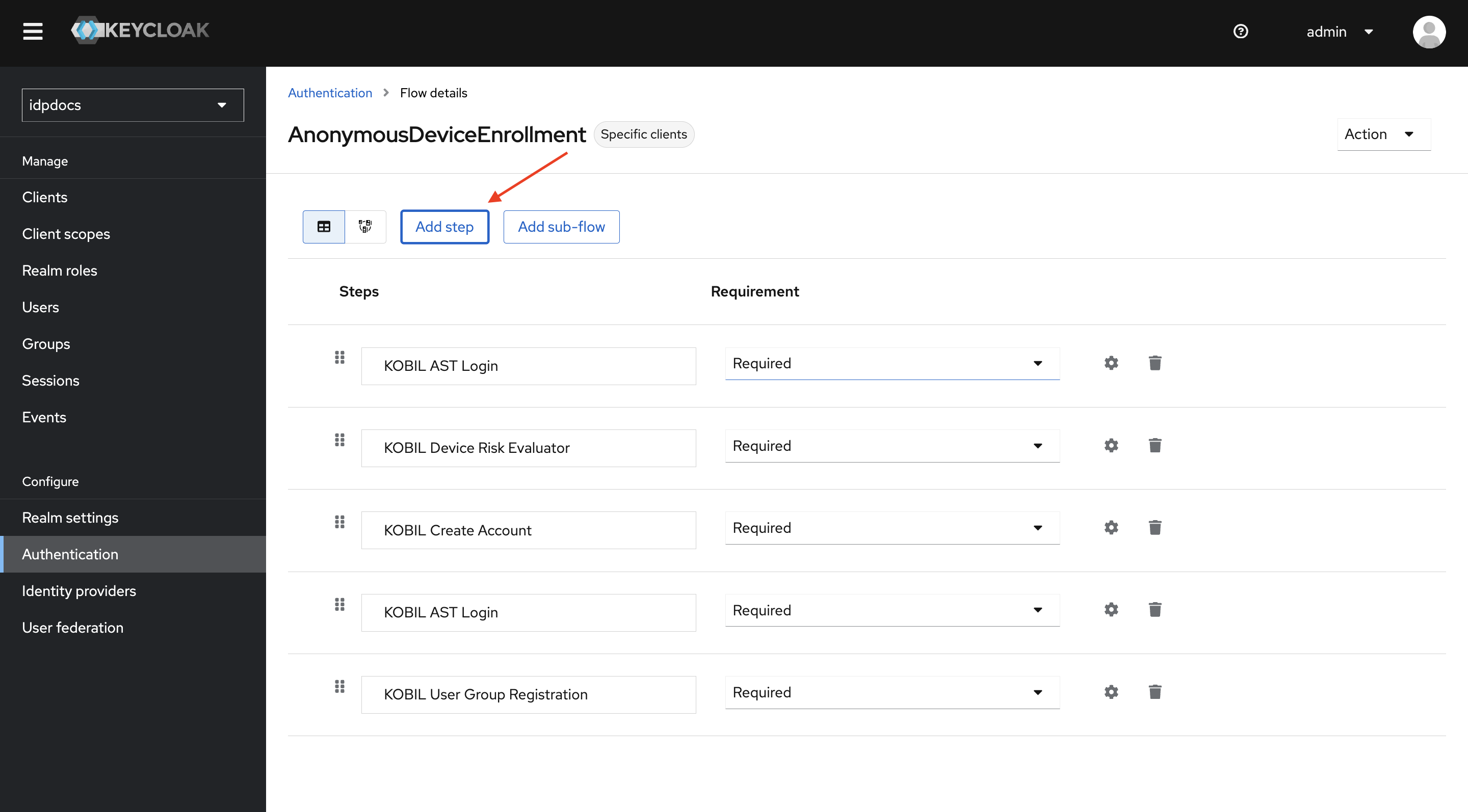
-
Click on Add step.
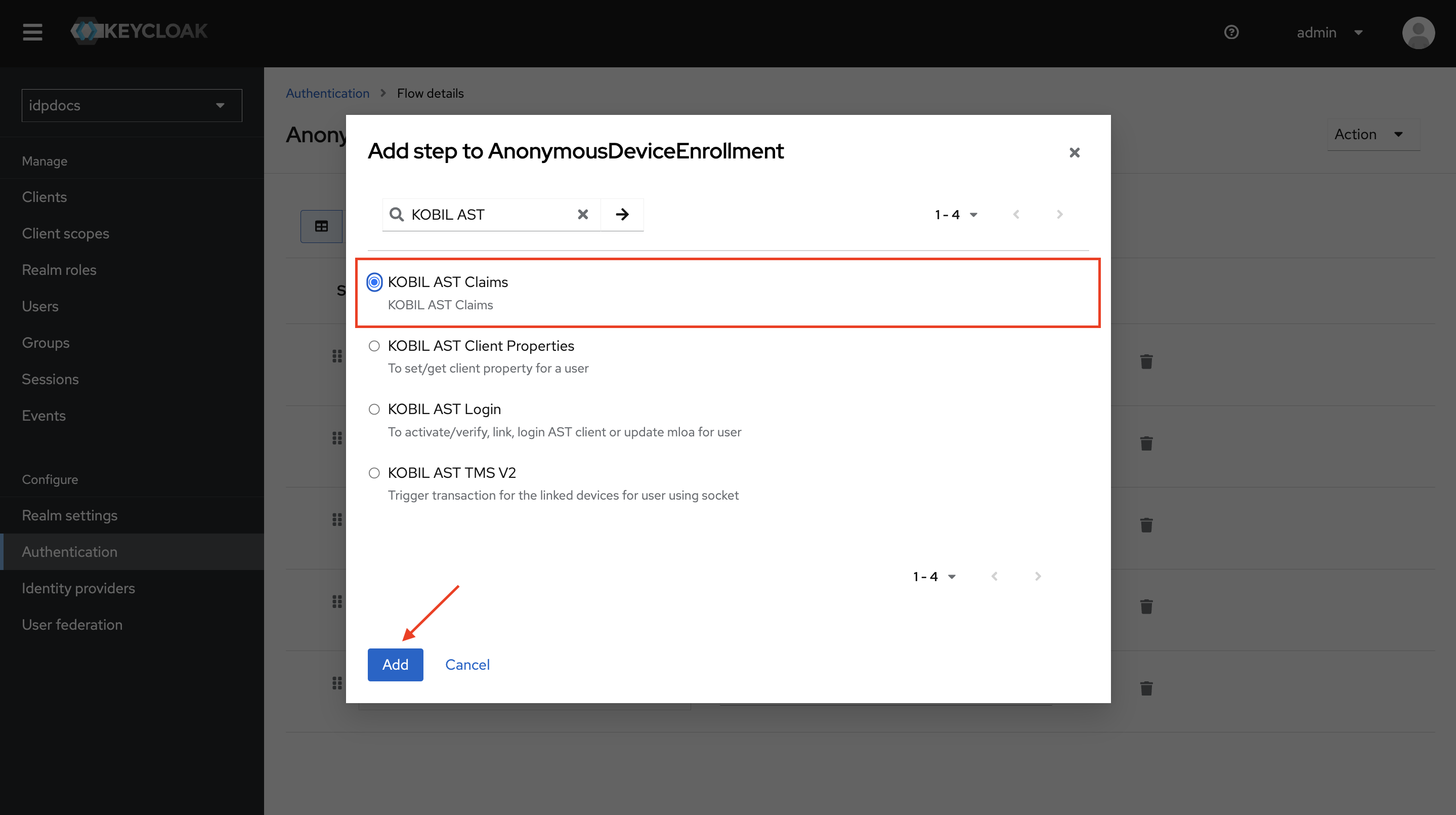
-
Select KOBIL AST Claims Authenticator and click Add.
-
Change KOBIL AST Claims Authenticator to required.
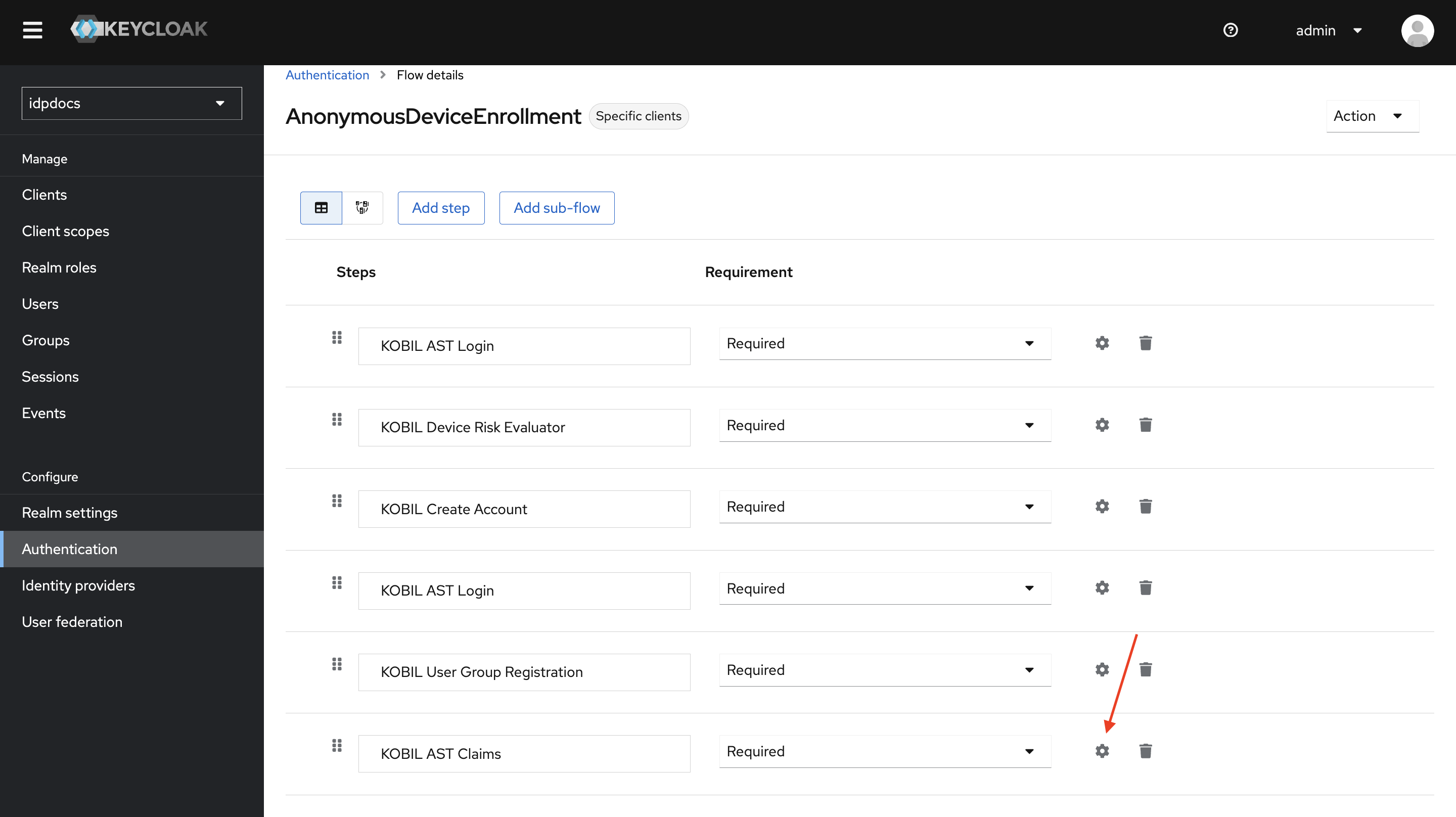
-
Select Settings icons of KOBIL AST Claims Authenticator.
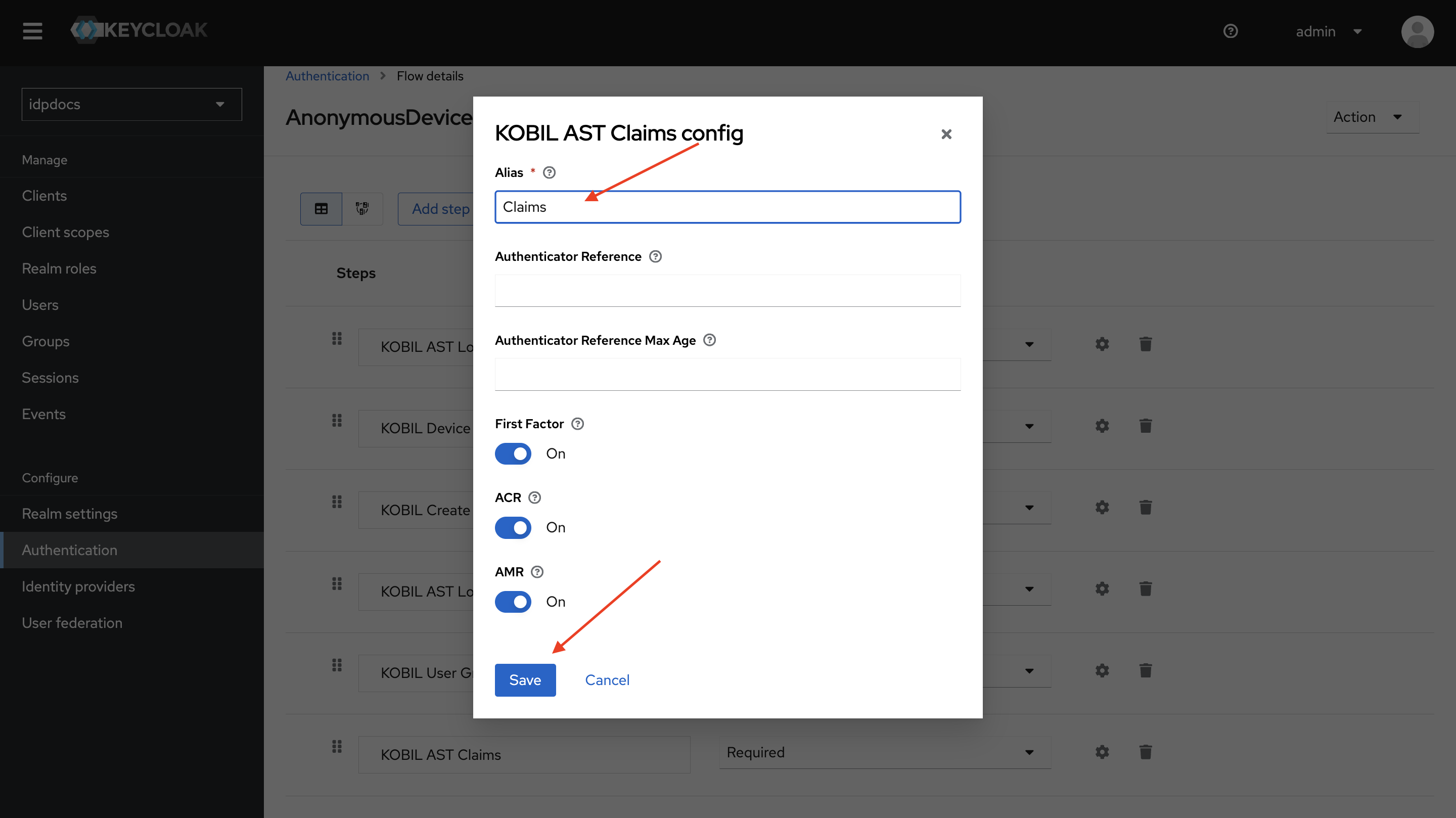
-
Enter Alias and click Save.
Authenticator Configuration
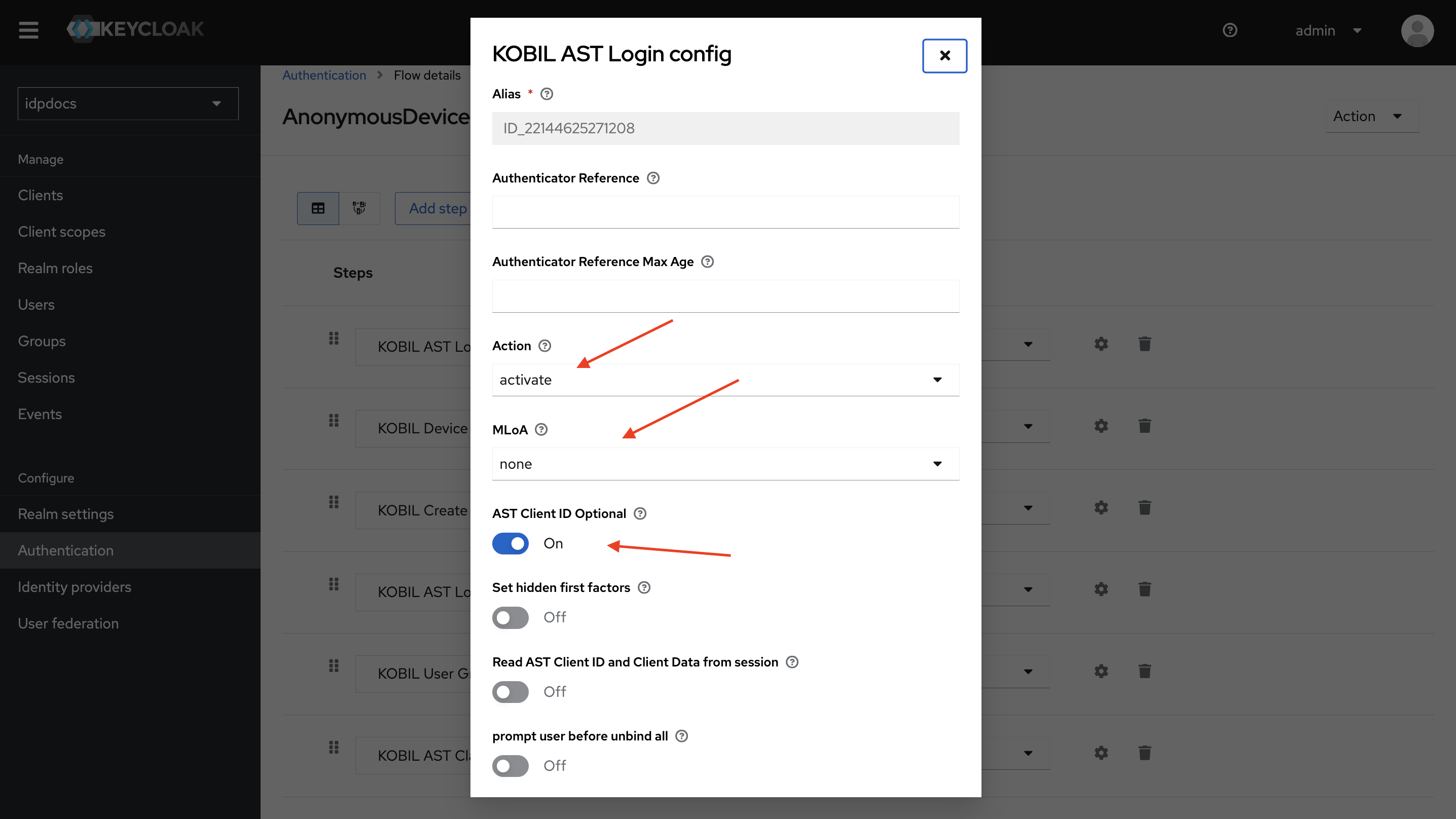
KOBIL AST Login (Activate)
AST Activation is performed using the AST Client ID (00000000000000000000000000) and AST Client Data. For more details about this authenticator, refer to the KOBIL AST Login Document.
Action
- The action config is set to Activate as we are performing AST Activation.
MLoA
- Set MLoA to None, as it is not required for AST Activation.
AST Client ID Optional
- Enabling this configuration allows flows to proceed without an AST Client ID in the header. If no AST Client ID is provided, the default null Client ID (00000000000000000000000000) will be used. Since this is an activation process, the AST Client ID is optional.
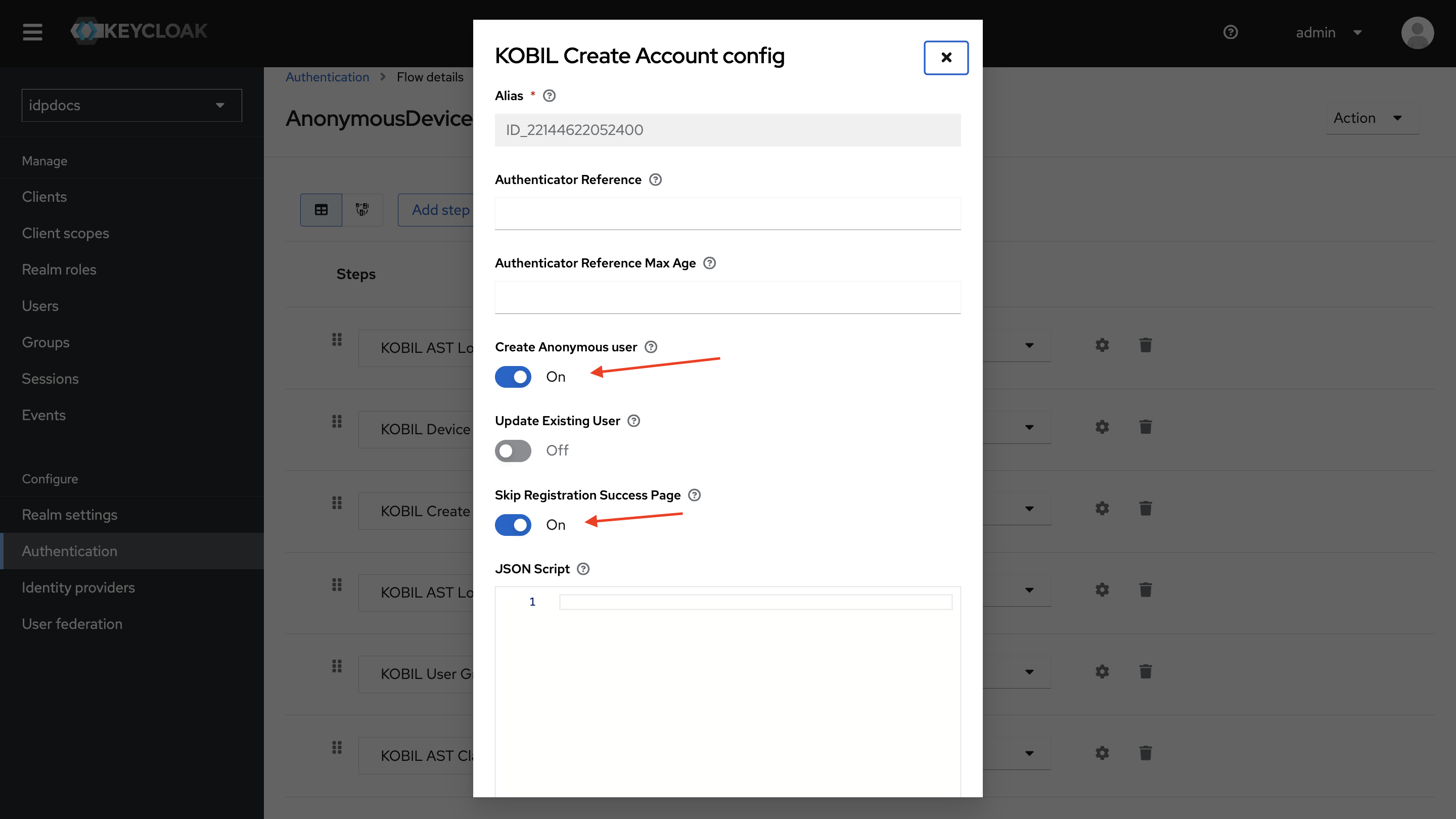
KOBIL Create Account
This Authenticator perform user creation in IDP. Please refer to KOBIL Create Account document for more details
Create Anonymous user
- Enable this configuration to create anonymous users in the IDP using a randomly generated UUID.
Skip Registration Success Page
- Enable this configuration to skip the success page after a successful user creation.
KOBIL AST Login (Link)
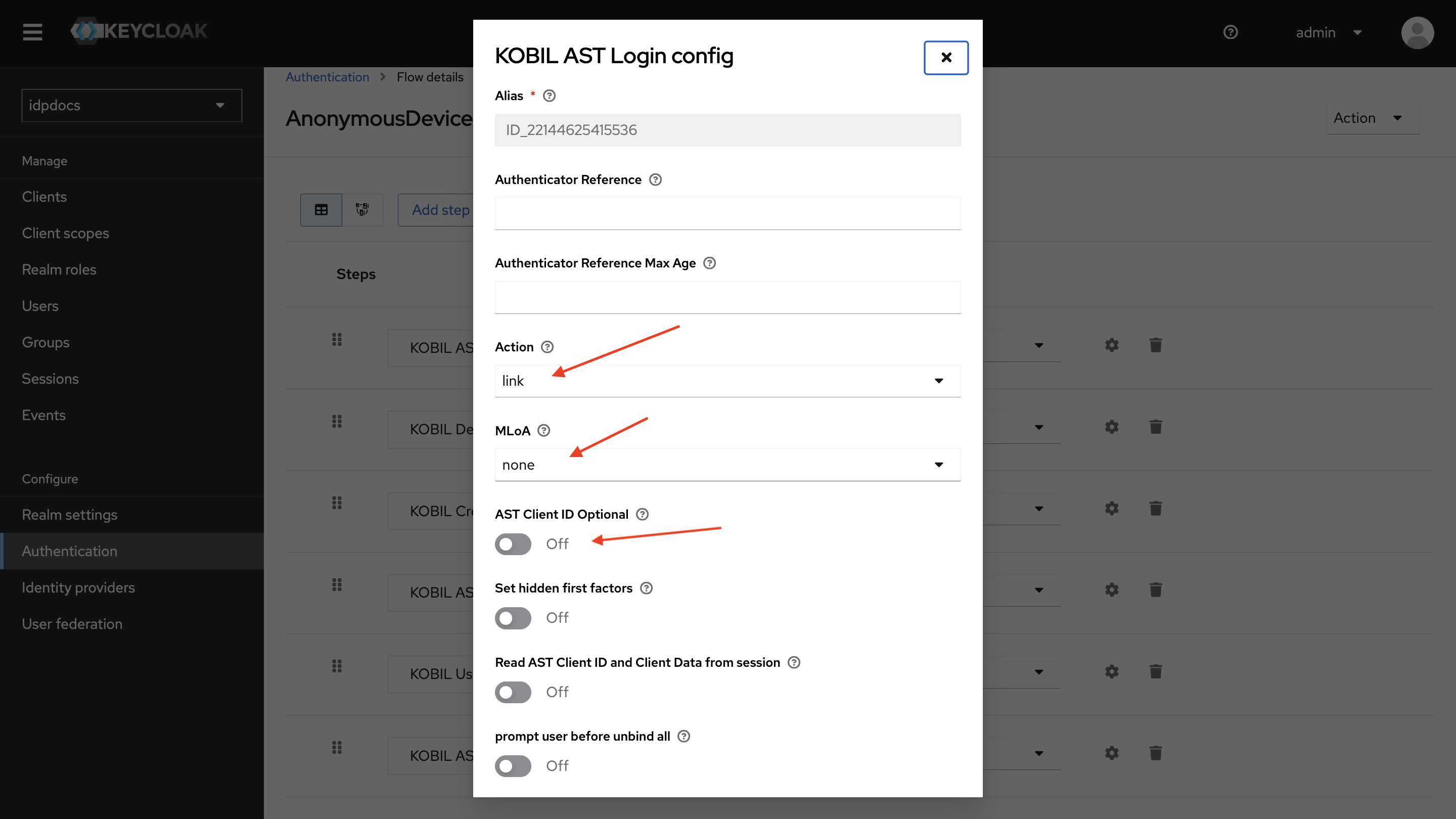
AST Link is performed using the AST Client ID and AST Client Data. For more details about this authenticator, refer to the KOBIL AST Login Document.
Action
- The action is set to Link as we are performing the AST Device Link.
MLoA
- Set MLoA to None since we are setting it as "none" when linking the user to the device.
AST Client ID Optional
- Keep this configuration disabled, as a valid AST Client ID and client data are required for the AST Link operation.
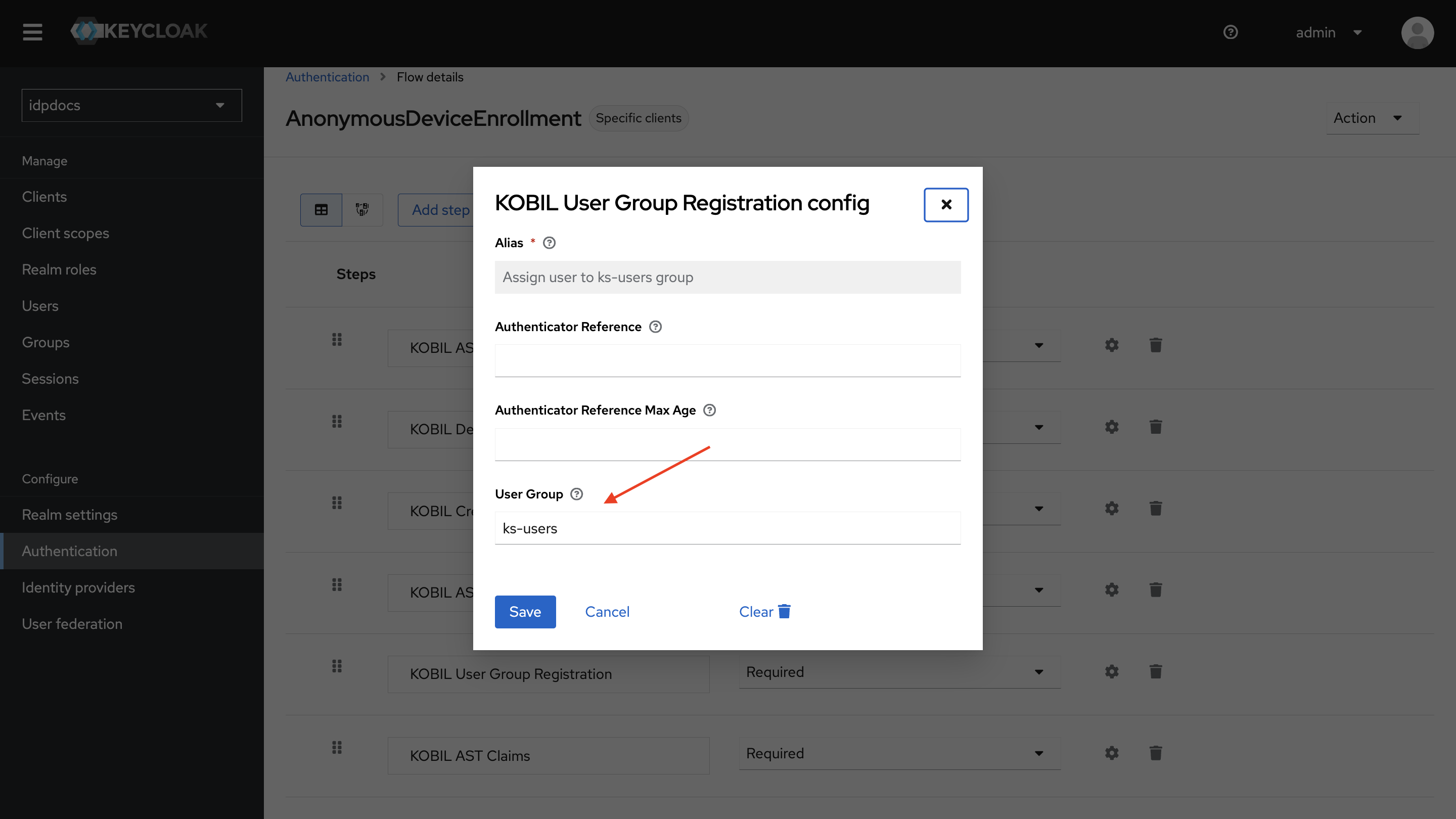
KOBIL User Group Registration
After successful user creation and device linking, the user is added to the configured user group. For more details, refer to the KOBIL User Group Registration Document.
User Group
- Set the intended user group, which in our case is ks-users.
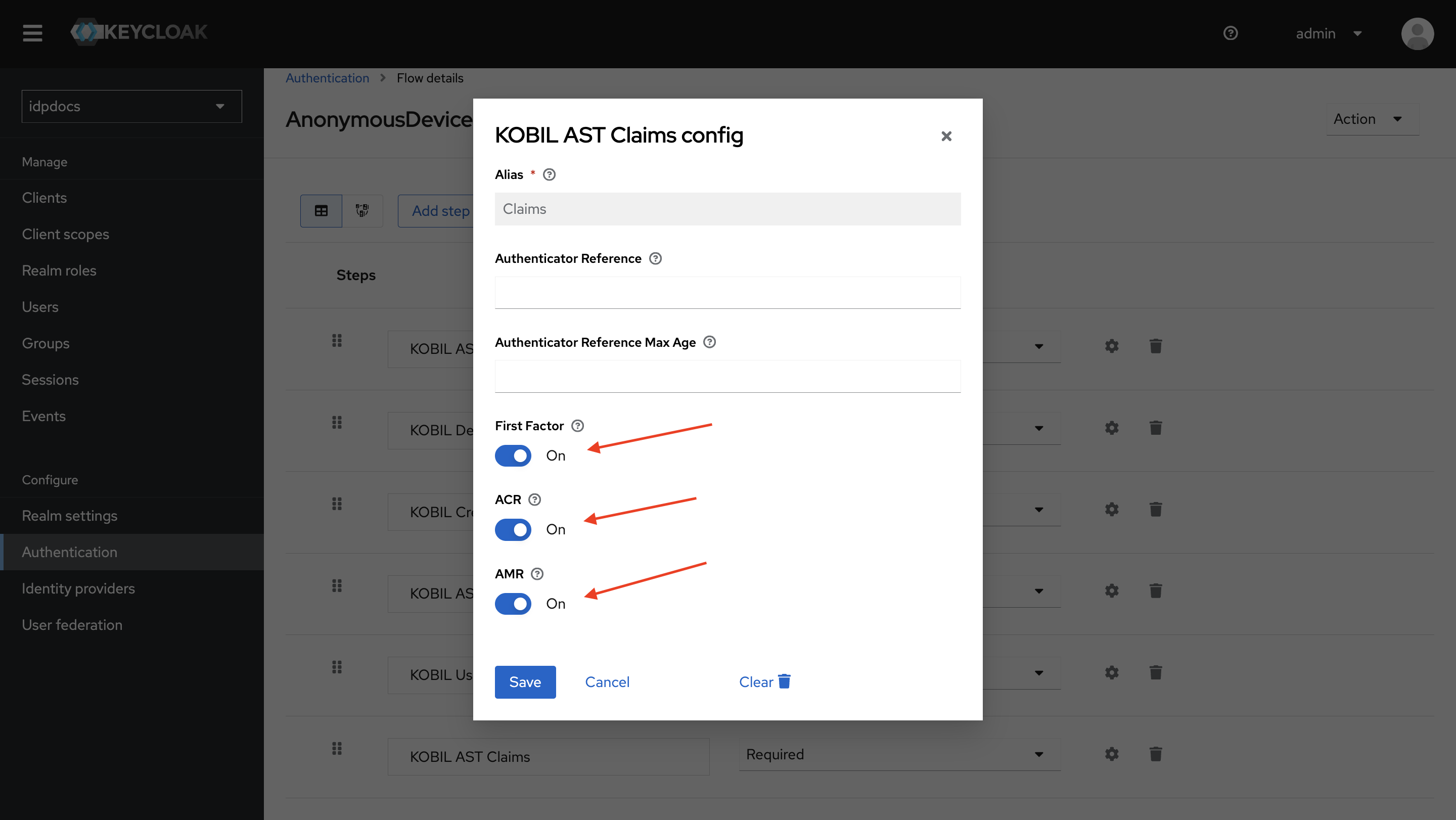
KOBIL AST Claims
It calculates ACR and AMR values based on the user's first and second factors and stores them in the session. For more details, refer to the KOBIL AST Claims Document.
First Factor
- Enable this to retrieve the user's first factor and store it in the session.
ACR
- Enable this to store the computed ACR value in the session.
AMR
- Enable this to store the computed AMR value in the session.