Installation Verification Procedure (IVP)
How to verify current installation is running
Info also available here: https://midprovider.developer.kobil.com/docs/documentation/monitoring
Verify IAM/IDP
Verification schema - IAM/IDP - docker runtime / kubernetes (more details below)
| Item | Specification | IAM/IDP | Value/info | expected data | comment | |
|---|---|---|---|---|---|---|
| Runtime/Processs | docker | docker hosted / kubernetes service | docker ps/logs/network | docker output | output shows started image, ports | verify port and image name |
| Sockets | TCP/IP | 443, 7600, 8443, 8444,,,, (kubernetes depends to ingress declaration) | LISTEN | |||
| API/responses | curl | https://master.api.<server_domain.net>/auth/realms/master/health/check | ||||
| Logs | docker log | IAM, Pooler, Connector, nginx | sudo docker logs -f <image_id> kubectl logs <pod> | using log-collector is better solution | ||
| GUI access | Browser | https://master.api.<server_domain.net>/auth/ |
- Pod/Image status (IAM requires multiple Images to run) (kubectl get pods -n <namespace>)
- network/socket status (kubectl get endpoints-n <namespace>)
- Rest/URL check https://master.api.<server_domain.net>/auth/realm/master/health/check
- GUI Login URL check https://master.api.<server_domain.net>/auth/
- expected Log data (see below / expected positive Log-data)
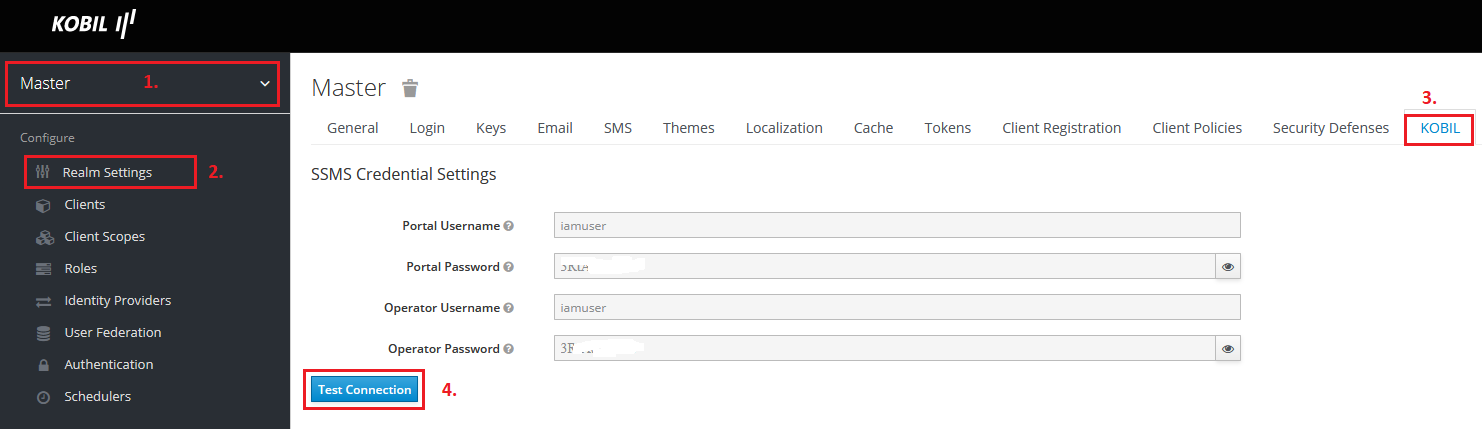
- Check for connectivity to Security Server via IDP login (from MASTER tenant - KOBIL pane / "Test Connection" / see Screenshot very below)
- "Integration Tools" (Connector and Pooler) - Pod status check
Verify Security Server
Verification schema - Security Server - OS-installed runtime / kubernetes (more details below)
| Item | Specification | IAM/IDP | Value/info | expected data | comment | |
|---|---|---|---|---|---|---|
| API/responses | curl/browser | https://ssms<server_domain.net>/ssms-services/asm/rest/device | expected positive | "ASM :-), https" | "ASM :-(, https" indicates problems | |
| API/responses | SOAP | See below MGT-Soap-Request per Basic_Auth(per Operator declaration) SVC-Soap-Request per Basic_Auth(per Portal declaration) | expected positive | see below | ||
| GUI access | Browser | https://<server.domain.net>/ssms-gui | ||||
| Logs | log file | <install-path>/home logs | checking / keywords | |||
| Runtime/Processs | native/OS | OS process / (on kubernetes depedent to ingress declaration) | ps -ef / k8s pod status | native OS tools | ps -ef | |
| Sockets | TCP/IP | 443, 8443, 8445,12001,, (kubernetes depends to ingress declaration) | LISTEN |
- Pod status/process list (kubectl get pods -n <namespace>)
- network/socket status (kubectl get endpoints-n <namespace>)
- Rest/URL check https://<ssms.server_domain.net>/ssms-services/asm/rest/device
- Soap-Call check for cluster status (see below for more details) - for OS-installer with specific Ports - for k8s-deployment all via https: per port 443 (depending on Ingress/Route declaration)
https://<ssms.server_domain.net>[:8443]/ssms-gui/soap/mgt/asm/AsmManagementWs
https://<ssms.server_domain.net>[:8445]/ssms-services/soap/svc/asm/AsmServicesWs - expected Log data (keywords)
- GUI Login URL check https://<ssms.server_domain.net>/ssms-gui/faces/login/login.jsp
Checking Security Server Services per SOAP
SVC Soap API access (GET request) per Kobil Security Server "Portal Service" declaration -- <Portal_user>@<tenant> - <password> (Note: Using Port-Number 8445 on native docker or OS-install only)
https://ssms.<server_domain.net\>[:8445]/ssms-services/soap/svc/svm/SvmServicesWs?wsdl
-- then enter user=(user@tenant] + password for portal service
MGT Soap API access (GET request) per Kobil Security Server "Operator" declaration -- <Operator_user>@<tenant> -- <password> (Note: using Port-Number 8443 on native docker or OS-install only)
https://ssms.<serverdomain.net\>[:8443]/ssms-gui/soap/mgt/kernel/KernelManagementWs?wsdl
-- then enter (Operator) user(user@tenant) + password for Operator login
SOAP-Call sample
<soapenv:Envelope xmlns:soapenv=http://schemas.xmlsoap.org/soap/envelope/ xmlns:ws=http://ws.asm.ssms.kobil.com/>
<soapenv:Header/>
<soapenv:Body>
<ws:getNodes/>
</soapenv:Body>
</soapenv:Envelope>
SOAP-Call Expected response ( 1MGT and 1 SVC instance)
<S:Envelope xmlns:S=http://schemas.xmlsoap.org/soap/envelope/>
<S:Body>
<ns2:getNodesResponse xmlns:ns2=http://ws.asm.ssms.kobil.com/>
<return>
<externalUrl>https://<Dummy 1>:443/ssms-services/soap/svc/asm/AsmServicesWs?wsdl</externalUrl>
<internalUrl>https://<Dummy 1>:8445/ssms-services/soap/svc/asm/AsmServicesWs?wsdl</internalUrl>
<nodeID>SSMS-D</nodeID>
<nodeState>ENABLED</nodeState>
<nodeType>SVC</nodeType>
<online>true</online>
</return>
<return>
<externalUrl>https://<Dummy 1>:443/ssms-gui/soap/mgt/asm/AsmManagementWs?wsdl</externalUrl>
<internalUrl>https://<Dummy 1>:8443/ssms-gui/soap/mgt/asm/AsmManagementWs?wsdl</internalUrl>
<nodeID>SSMS-D</nodeID>
<nodeState>ENABLED</nodeState>
<nodeType>MGT</nodeType>
<online>true</online>
</return>
</ns2:getNodesResponse>
</S:Body>
</S:Envelope>
Checking IAM/Security Server Service integration from IAM-GUI: